BidLight User, Roles & Permissions
The User, Roles, and Permissions feature is a critical component of the platform’s administrative tools, providing a structured approach to managing user access and capabilities within the system. This feature allows administrators to define roles, assign users to these roles, and control the permissions each user has, ensuring that the right individuals have the appropriate level of access to various functionalities and data. Below is a detailed report on the functionalities provided by this feature.
Features Overview : -
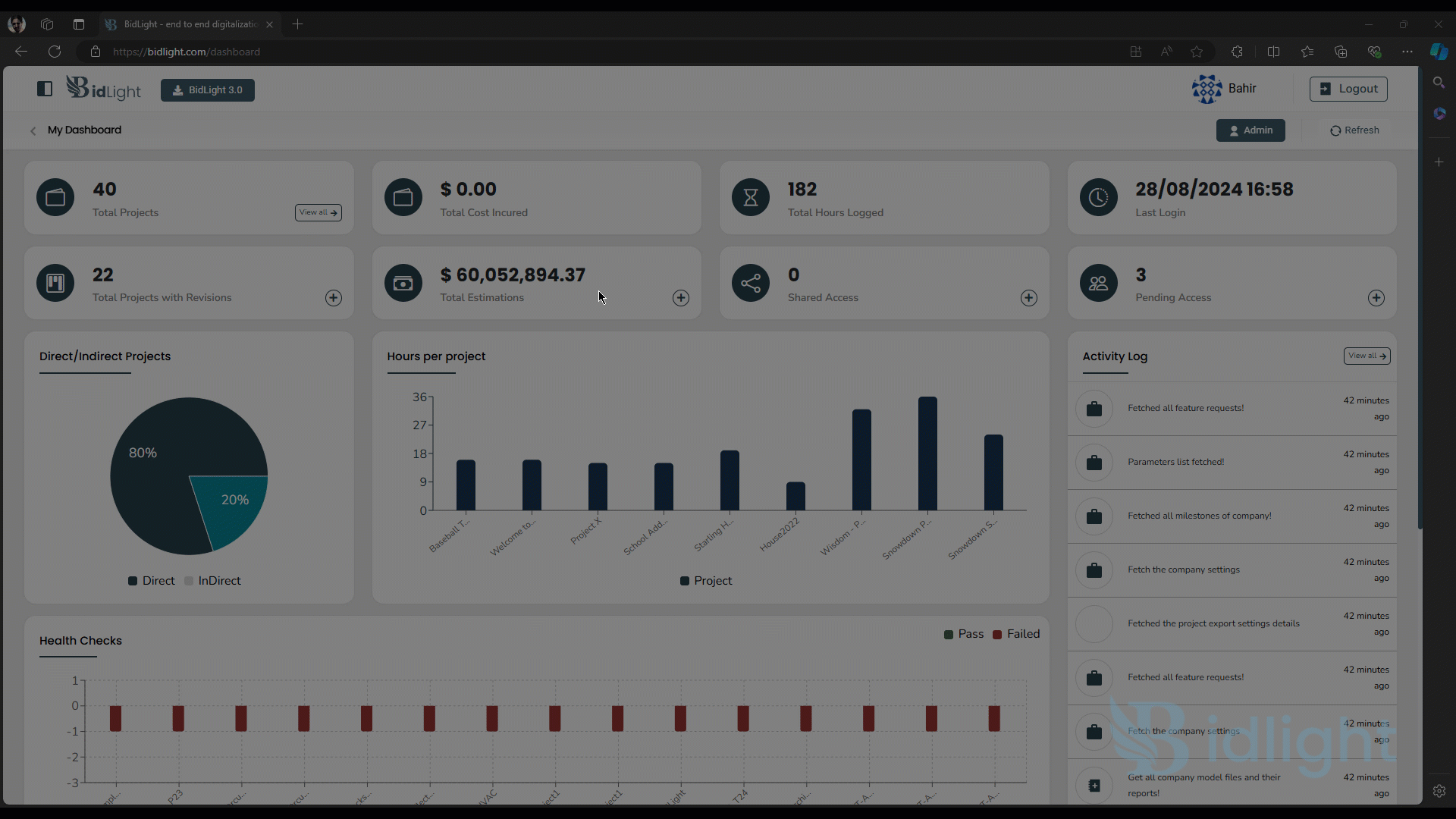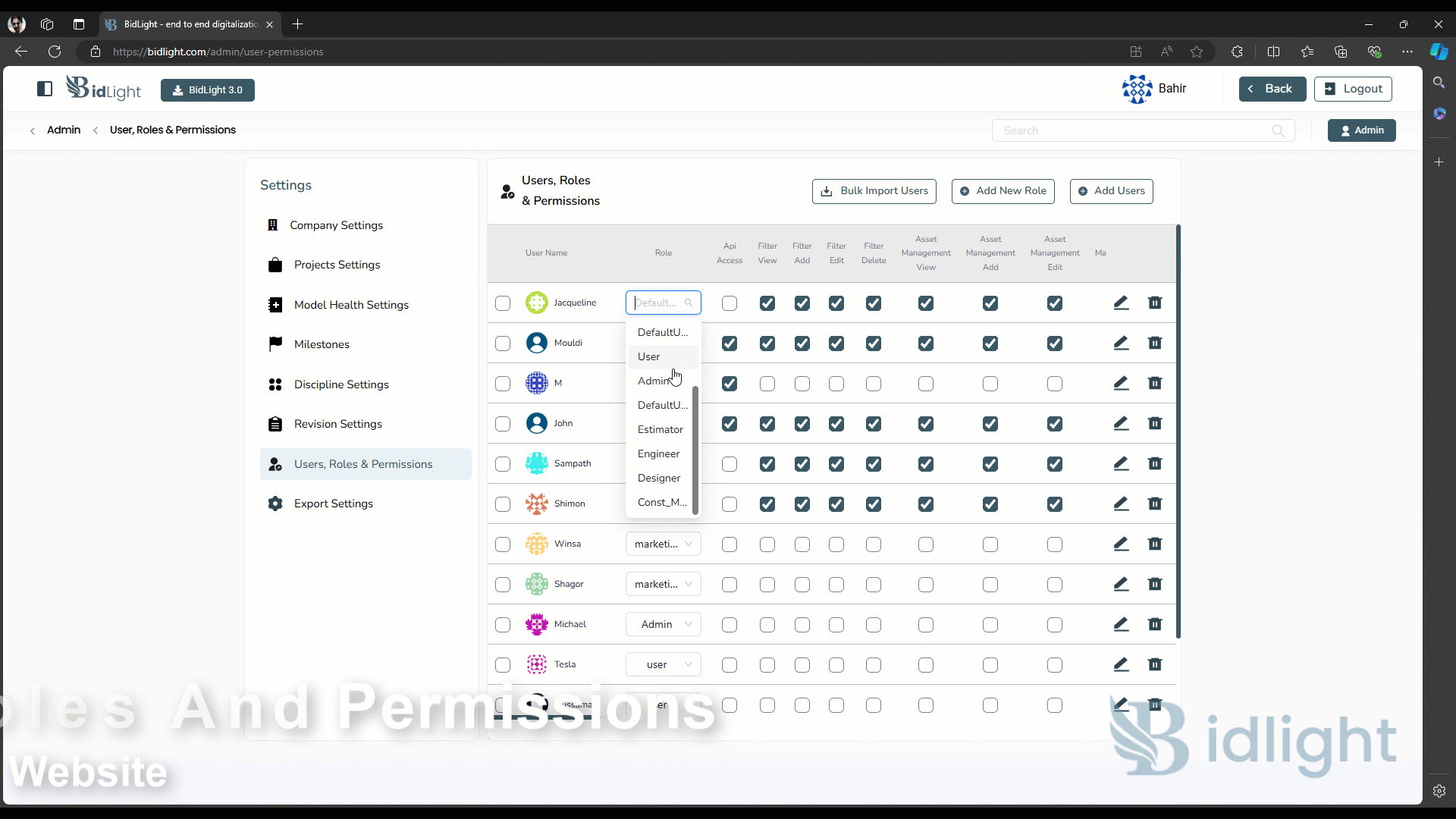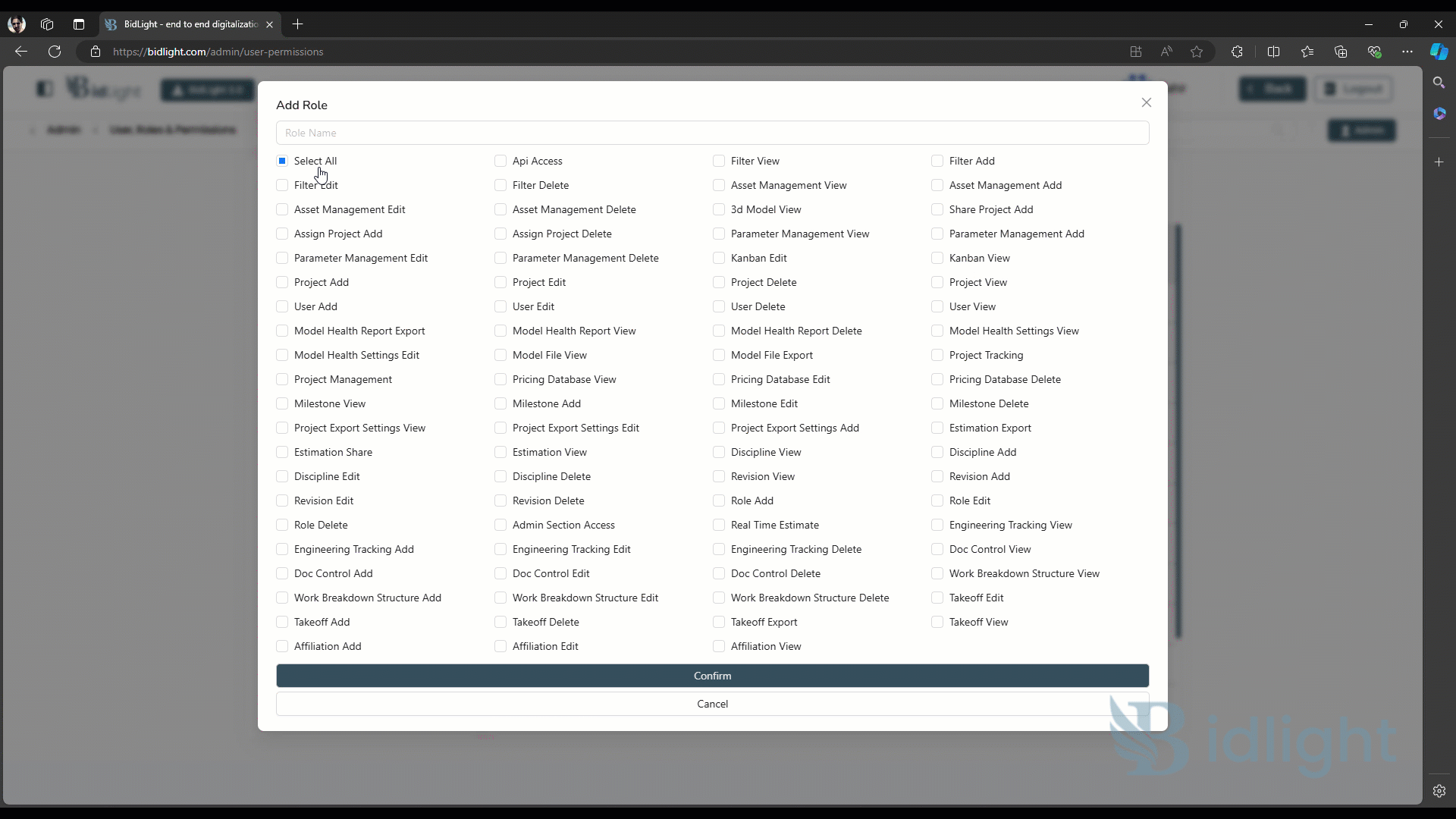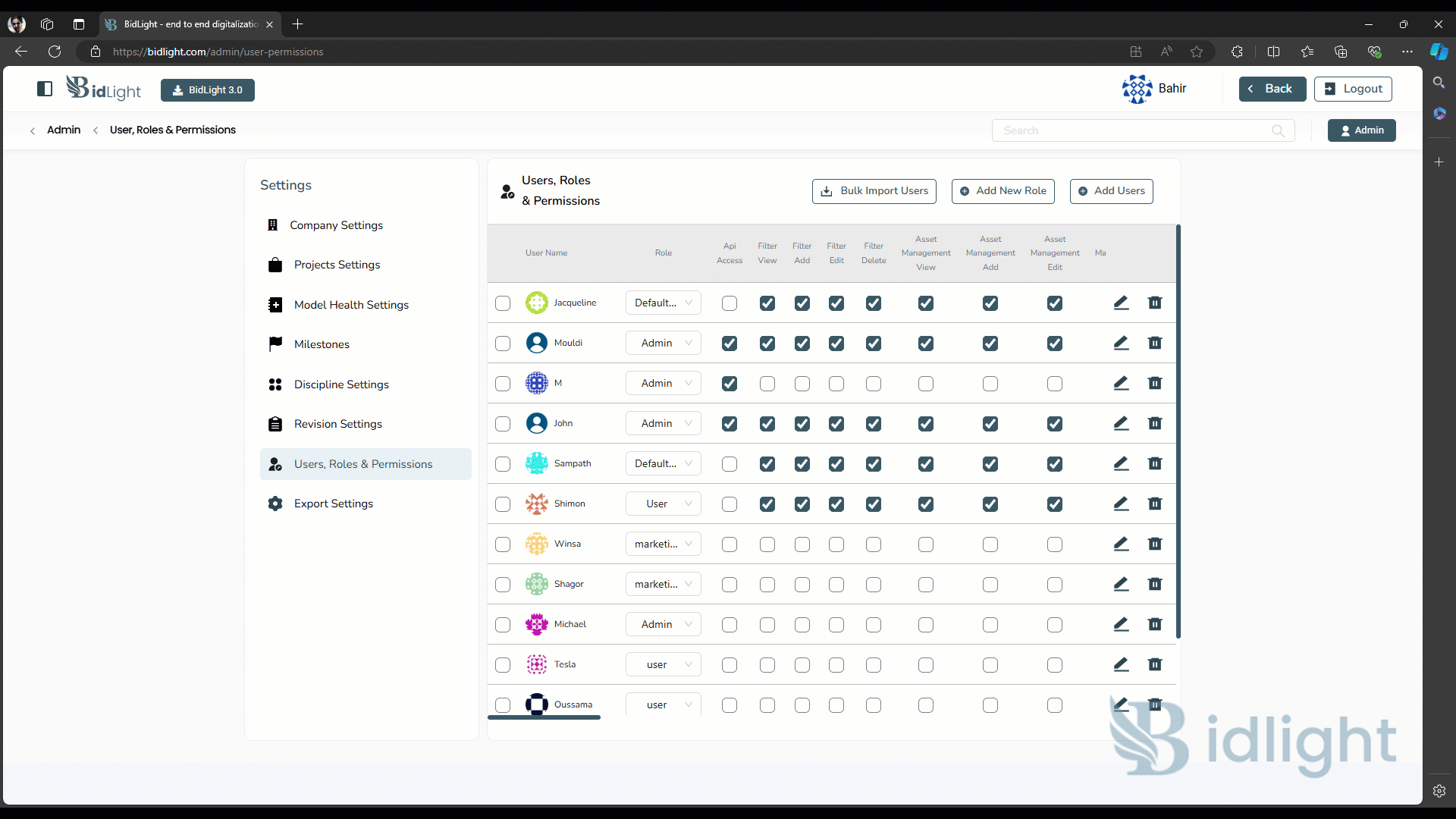
1. Add Role
● Role Definition: Administrators can create new roles within the platform to align with the organization’s structure and requirements. Each role is defined by a set of permissions that control what users assigned to that role can see and do within the system.
● Customizable Permissions: When creating a role, administrators can select from a wide range of permissions. This allows for fine-grained control over access to features such as document management, project tracking, data editing, and reporting.
● Role Hierarchy: The platform supports hierarchical roles, where certain roles may inherit permissions from other roles. This helps streamline the process of role creation and ensures consistency in permission levels across the organization.
● Role Description: Each role can include a description that outlines its purpose and the key responsibilities associated with it. This helps ensure that the roles are clearly understood by both administrators and users.
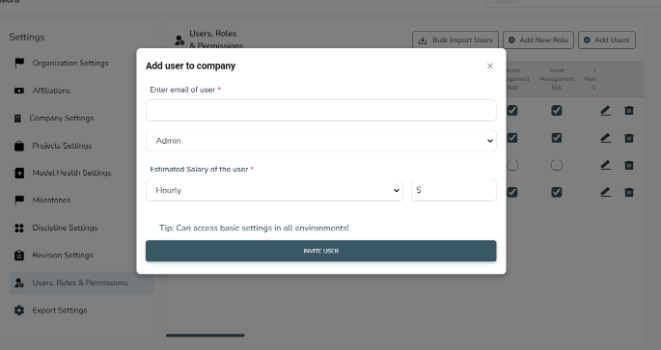
2. Add User
● User Creation: Administrators can add new users to the platform by providing essential information such as the user’s name, email address, and contact details. The user is then assigned to one or more roles based on their responsibilities.
● Role Assignment: During user creation, administrators can assign the new user to one or more predefined roles. This automatically grants the user the permissions associated with those roles, ensuring they have the appropriate level of access from the start.
● Invitation and Onboarding: Once a user is added, they receive an invitation email with instructions on how to access the platform. The onboarding process can be customized to include tutorials or guides, helping new users get up to speed quickly.
● User Profile Customization: Users can customize their profiles by adding personal information, setting up their preferences, and managing their password. This ensures that each user’s experience is tailored to their needs.
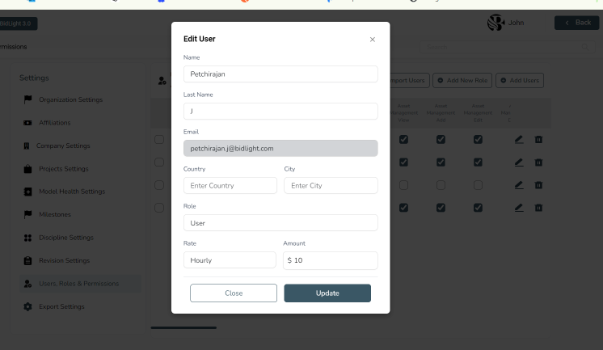
3. Edit User
● User Information Update: Administrators can edit existing user profiles to update contact information, change roles, or modify permissions. This is particularly useful when users’ responsibilities change or when correcting any errors in the initial setup.
● Role Reassignment: If a user’s responsibilities change, administrators can easily reassign them to different roles, thereby updating their permissions. This ensures that users always have access to the tools and data they need for their current tasks.
● Status Management: Administrators can activate or deactivate user accounts as needed. Deactivated users are temporarily suspended from accessing the platform, which is useful for managing temporary leaves or when users no longer require access.
● Audit Trail: The platform maintains an audit trail of all changes made to user profiles, including who made the changes and when. This provides accountability and helps administrators track modifications over time.
4. Delete User
● Safe Removal: Administrators can delete users who no longer need access to the platform. Before deletion, the platform may prompt the administrator to reassign the user’s tasks or data to other users to ensure continuity.
● Data Preservation: While the user account is deleted, the platform ensures that any data or records associated with the user are preserved. This is critical for maintaining project continuity and ensuring that historical data remains intact.
● Access Termination: Once a user is deleted, their access to the platform is immediately revoked. The system ensures that the user can no longer log in or interact with the platform, protecting sensitive information from unauthorized access.
● Confirmation Process: To prevent accidental deletions, the platform includes a confirmation step where administrators must confirm their intent to delete a user. This reduces the risk of unintentional loss of user accounts.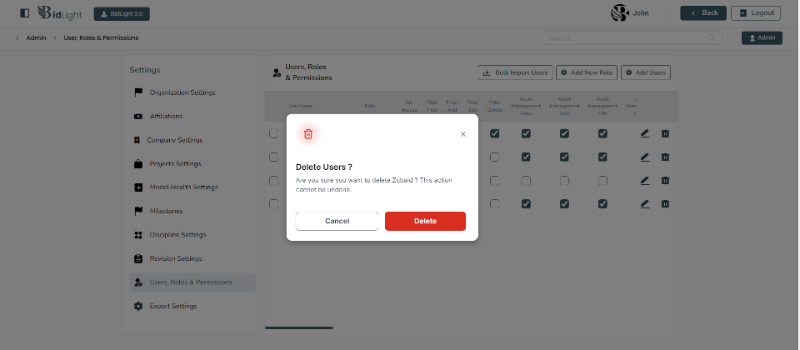
5. Provide Permissions
● Granular Permission Control: The platform allows administrators to provide permissions at a granular level. This means they can control access to specific features, data sets, or actions within the platform, tailoring each user’s experience to their role.
● Permission Groups: Permissions can be grouped into categories for easier management. For example, there might be groups for document management, reporting, or project management. This simplifies the process of assigning permissions to roles.
● Dynamic Permissions: Permissions can be updated dynamically, meaning that changes to permissions are applied in real-time. This is crucial for adapting to changing project needs or organizational structures without requiring users to log out and back in.
● Inherited Permissions: Roles can inherit permissions from other roles, creating a hierarchical structure. This is useful for ensuring consistency across similar roles and reducing the administrative burden of managing permissions individually.
● Permission Audits: Administrators can conduct regular audits of permissions to ensure that users have the appropriate level of access. This is particularly important in large organizations where roles and responsibilities may frequently change.
6. User Interface and Experience
● Intuitive Interface: The User, Roles, and Permissions feature is designed with a user-friendly interface that simplifies the process of managing access. The layout is straightforward, with clear options for adding, editing, and deleting users and roles.
● Search and Filter Options: The platform provides robust search and filter functionalities, allowing administrators to quickly locate specific users, roles, or permissions. This is especially useful in large organizations with many users.
● Bulk Actions: For efficiency, the platform supports bulk actions, enabling administrators to update roles or permissions for multiple users simultaneously. This feature saves time and reduces the need for repetitive tasks.
● Notifications: The platform can send notifications to administrators when changes are made to users, roles, or permissions. This helps keep the administrative team informed of updates and ensures that changes are monitored.
7. Benefits
● Enhanced Security: By providing granular control over user access, the platform ensures that sensitive data is protected and only accessible to authorized personnel. This reduces the risk of data breaches and unauthorized actions.
● Improved Efficiency: The ability to quickly add, edit, and delete users and roles, along with the provision of dynamic permissions, streamlines administrative tasks and reduces the time needed to manage user access.
● Flexibility: The platform’s flexibility in managing roles and permissions allows organizations to adapt quickly to changing needs, ensuring that users always have the tools and access they require to perform their tasks effectively.
● Accountability: The detailed audit trails and logging of changes to users, roles, and permissions ensure accountability, making it easy to track who made changes and when, which is crucial for compliance and security audits.
Conclusion
The User, Roles, and Permissions feature is a powerful tool that provides organizations with the flexibility and control needed to manage user access effectively. By supporting the creation of roles, assignment of users, and granular control of permissions, the platform ensures that each user has the appropriate level of access to perform their tasks efficiently. The feature’s user-friendly interface, real-time updates, and robust security measures make it an essential component of the platform’s administrative toolkit, supporting both small teams and large organizations in managing their user base with confidence and precision..